AI & HPC Data Centers
Fault Tolerant Solutions
Integrated Memory
Protection and security are critical for memory encryption to prevent unauthorized access, data theft, and compliance failures, especially in cases of device loss or theft.

Advanced Encryption Standard (AES) is a hardware-based encryption method for converting data from an unencrypted into an encrypted format. 256 bits encryption key length makes it virtually impossible to decrypt the data without the original key.
Data can be easily retrieved and misused by unauthorized users. The loss or theft of data can lead to severe consequences. A growing demand for SSD encryption is now more popular than ever, especially in the industrial embedded applications where data generated is highly sensitive and confidential.
AES is a symmetric encryption algorithm. AES supports a block length of 128 bits and key lengths of 128, 192, and 256 bits. SMART adopts AES-256 Encryption that supports the largest bit size, and is practically unbreakable based on the current computing power, making it the strongest encryption standard.
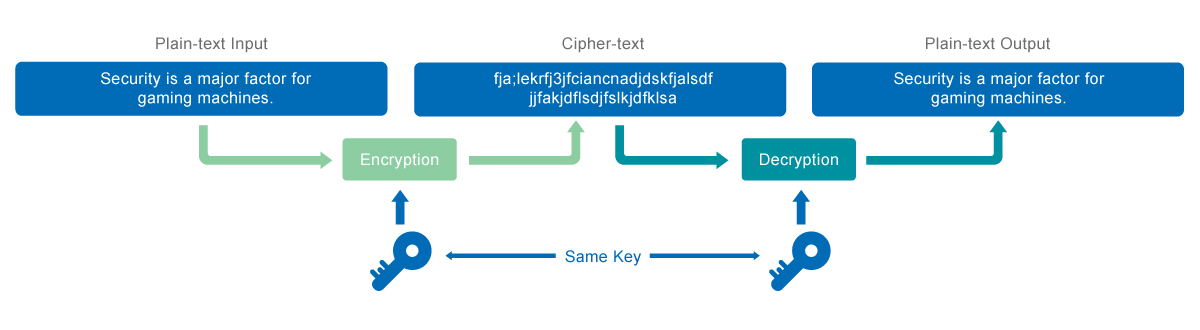
When the host writes data to the Flash storage device, a Random Number Generator (RNG) generates a 256-bit symmetric cipher key which is passed to the AES engine. The AES engine encrypts the plain text into cipher text and sends it to the NAND Flash for storage.
To retrieve the data from the storage device, the AES engine decrypts the cipher text in the NAND Flash, and then transmits data to the host as plain text. The encryption and decryption processes are done at the Flash level.
Trusted Computing Group (TCG), a non-profit international organization, develops, defines, and promotes open standards and specifications for secure computing. The Opal Storage Specification is a set of security specifications for features of data storage devices that enhance their security. The latest Opal Storage Specification is currently available in version 2.0.
TCG Storage Work Group created the Opal Security Subsystem Class (SSC) as one class of security management protocol for storage devices. It is the most recognized standard for self-encrypting drives (SEDs). SMART offers TCG Opal 2.0 compliant self-encrypting SSDs incorporating AES encryption for rock-solid data protection.
The hardware-based encryption offers the advantages over software-based encryption in terms of performance, security, and management. TCG Opal defines security specifications for storage drives, while the most common approach to data encryption is AES encryption technology. With the integration of AES encryption, Self-Encrypting Drives (SED) compliant with TCG OPAL 2.0 featuring pre-boot authentication and LBA-specific permission effectively prevent data from being stolen or tampered with by a hardware-based encryption method.

Write Protection prevents drives from unauthorized data write via a hardware switch/pin or software command. With the write protection feature, users are guaranteed that their data cannot be over-written on the Flash device by triggering the write-protect function.
Write Protection helps prevent data from being accidentally overwritten or erased. It’s a locking mechanism which prevents modification or deletion of data on a storage device. Generally, once your SSD or other storage devices are write-protected, you are not allowed to delete or edit data or files.
Write Protection can be enforced using either software or hardware. It’s usually a hardware switch in the case of diskettes to toggle write-protection of the entire drive. In addition to the hardware switch, Write Protection can also be triggered through firmware commands which can be customized depending on customers' requirements.

Secure Erase is an action to completely erase user’s data from the SSDs. This feature will entirely reset all the SSD storage blocks to empty and prevent any important data from leaking.
When it comes to data, it is important to know how it is erased and if it is completely and securely erased. Many software utilities can erase data securely, however, Secure Erase command is supported by the National Institute of Standards and Technology (NIST) as an acceptable way of sanitizing data. As a data sanitization, Secure Erase commands can completely overwrite all of the data on a storage medium. No file recovery program, partition recovery program, or other data recovery methods will be able to extract data from the drive.
When the Secure Erase command is given to the SSD, it will initial an action to completely erase user’s data from the drive. This feature will completely reset all the SSD storage blocks to empty and restore the drive to its original state.
SMART Modular Technologies helps customers around the world enable high performance computing through the design, development, and advanced packaging of integrated memory solutions. Our portfolio ranges from today’s leading edge memory technologies to standard and legacy DRAM and Flash storage products. For more than three decades, we’ve provided standard, ruggedized, and custom memory and storage solutions that meet the needs of diverse applications in high-growth markets. Contact us today for more information.


At Penguin, our team designs, builds, deploys, and manages high-performance, high-availability HPC & AI enterprise solutions, empowering customers to achieve their breakthrough innovations.
Reach out today and let's discuss your infrastructure solution project needs.